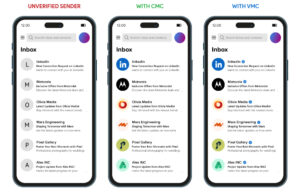
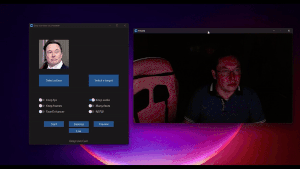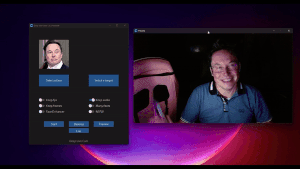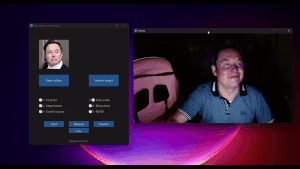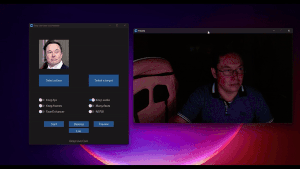
#PacketHunters: holiday attacks don’t exploit systems, they exploit absence (yours)
Holiday periods create ideal conditions for identity-based attacks: reduced monitoring, delayed response, and persistent access. This PacketHunters analysis explains why attackers prefer holidays and how identity abuse accelerates when vigilance drops.